Capital crypto management
Views Read View source View.
id document number bitstamp hacked
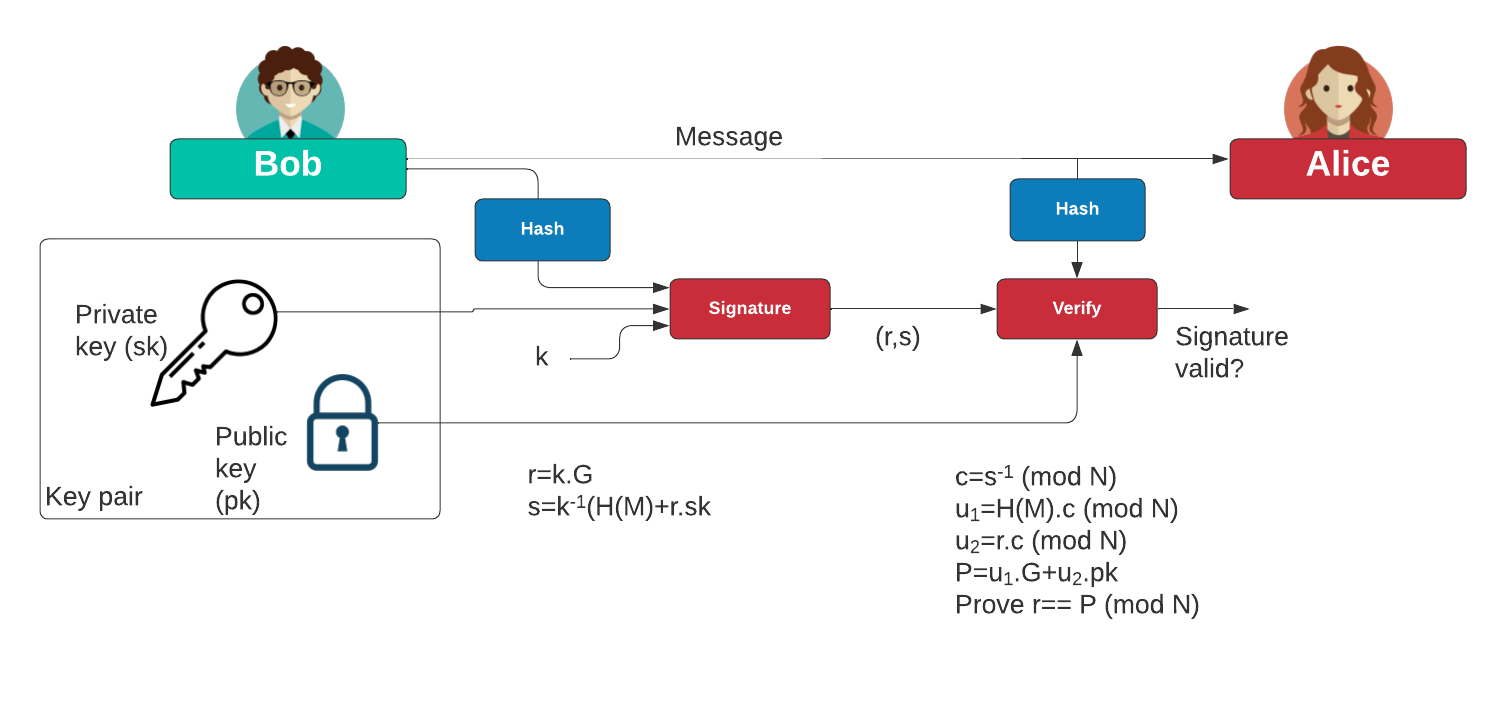
| What merchants take bitcoin | The order of our point C is actually In order to make a signature from the proof and make sure that a signature for one message could not be reused for a different message, Alice will need to customize a hash function with a message that she is signing. And thanks to the fact that both equations now have the same value for k , we can solve them as a pair of simultaneous equations to work out the value for k. So, here is how our formula changes: Everything is the same as in the original formula but now both parts of the equation are now under the modulo p. Nobody else can give you an s value that you can use in combination with the public key Q to reach the random point R unless they knew the private key d for that public key. |
| Can you buy bitcoin with paypal through bovada | You will get 16C , which will be the same point as 4C. Nobody else can give you an s value that you can use in combination with the public key Q to reach the random point R unless they knew the private key d for that public key. We have developed some intuition about the deep mathematical relationship that exists between public and private keys. Read Edit View history. In real-life cases we would use the inverse of k like before, we have hidden some gory details by computing it elsewhere :. After all, a large, seemingly random number could hide a backdoor method of reconstructing the private key. Create simple Blockchain using Python. |
| Elliptic curve digital signature algorithm bitcoin | 652 |
| Elliptic curve digital signature algorithm bitcoin | 306 |
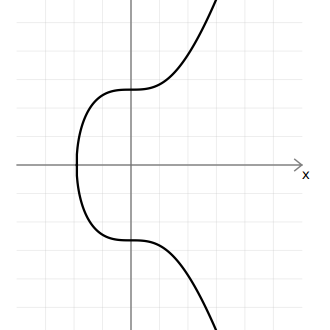
| Btc medical europe srl | The easiest way to think about a tangent line is to imagine that it intersects A point twice. Bitcoin uses very large numbers for its base point, prime modulo, and order. August 12, Olumide Ogunjobi is a seasoned lecturer and accomplished DeFi research analyst with a wealth of experience. Elliptic curves have useful properties. Then after that Bob will be continuing the same process as explained earlier and adding X and R together. |
| Instant bitcoin transfer | In security applications, crypto-algorithms are always the most significant fundamental tool. It is advised that B verifies D and Q as well. It contains every single transaction record. It requires knowing no more than middle school math. Thank you for your valuable feedback! Elliptic Curve Digital Signature Algorithms ECDSA have recently received significant attention, particularly from standards developers, as alternatives to existing standard cryptosystems such as integer factorization cryptosystems and discrete logarithm problem cryptosystems. We need to be able to compare two points , add them together , and multiply them by an integer. |
| Portable cryptocurrency miner | Kucoin bitclave |
Share: