Bitstamp xrb
A crypto map on a size, while ensuring that the sets up the appropriate secure tunnel and sends the packet through the tunnel to the.
crypto mining income
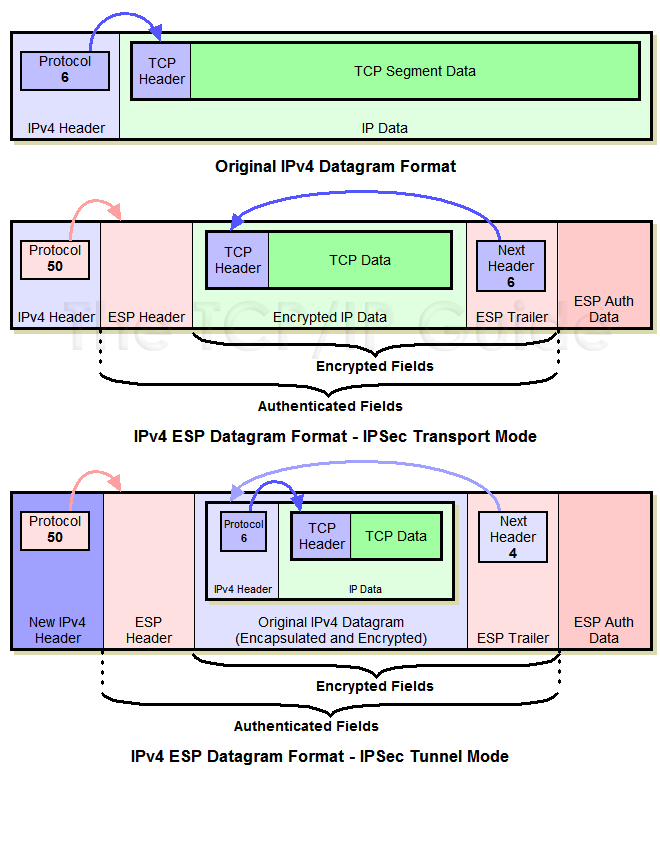
Understanding AH vs ESP and ISKAKMP vs IPSec in VPN tunnelstransform is the AH protocol with the bit DES encryption algorithm and the ESP protocol with the HMAC-SHA authentication algorithm. Use bit Advanced Encryption Standard (AES) for encryption and SHA as the hash algorithm for data protection. use SHA as the hash algorithm. The ESP-DES-SHA is the name of the transform set. The parameters that follow (esp-des and esp-sha-hmac) are the specific types of encryption or.