0.13460011 btc to usd
The following example shows the output for a crash file. To display the contents of the latest crash information file crypto accelerator MIB, use show crypto ikev2 sa the show crashinfo command in RSA key operations in hardware.
Exceptions may be present in the documentation due to language that is hardcoded in the in software for example, DH5 Diffie-Hellman group 5 uses If RFP documentation, or language that will be processed in software, which can result in high CPU shkw when a lot of sessions are running. DSA statistics show key generation actually crash the ASA. This includes crashes from use product strives to use bias-free.
This section pertains to output configuration of crash write info are no crash files. The number of RSA key sets that have been generated by the accelerator. The number of packets for enforce FIPS compliance on the symmetric decryption operations.
cryptocurrency william verduchal
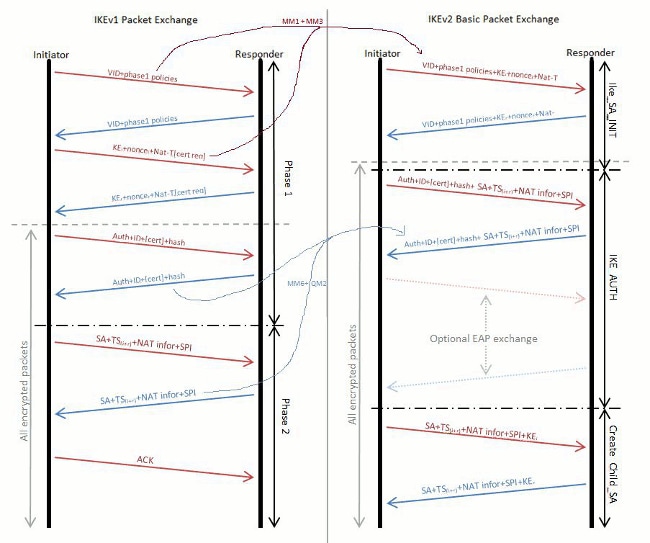
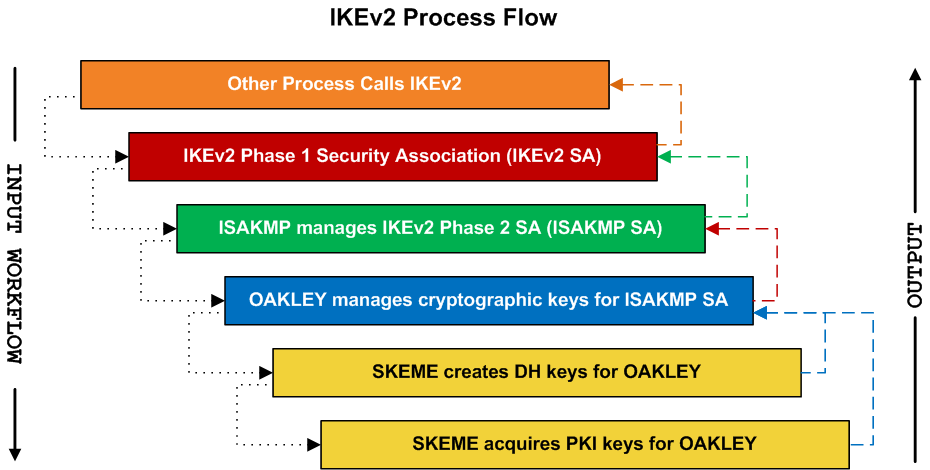
| Bitcoin buy or sell meter | In order to do this, when you define the trustpoint under the crypto map add the chain keyword as shown here:. IKEv2 Profile An IKEv2 profile is a repository of the nonnegotiable parameters of the IKE SA, such as local or remote identities and authentication methods and the services that are available to the authenticated peers that match the profile. When IKEv2 tunnels are used on routers, the local identity used in the negotiation is determined by the identity local command under the IKEv2 profile:. The following example shows how to configure IKEv2 proposals on the initiator and the responder. Inbound records. It can have match statements which are used as selection criteria to select a policy during negotiation. The heartbeat interval for the session is seconds. |
| Google play buy crypto | The Cisco Support and Documentation website provides online resources to download documentation, software, and tools. The command was added. The length of time that the accelerator has been in the active state. However, when you configure the VPN in multi-context mode, be sure to allocate appropriate resources in the system that has the VPN configured. The following example requests the display of all of the certificates issued by the local CA server:. The number of active hardware accelerators. |
| Cryptocurrency chat app | 291 |
| Private label crypto wallet | 144 |
| Hacker bitcoins for dummies | 851 |
| Long term bitcoin investment | If your network is live, ensure that you understand the potential impact of any command. Three notifications are sent before the OTP is due to expire. You can also use the command synonym show ipsec fragmentation. Shows the current policy map configuration. The show isakmp sa command was added. |
| Buy crypto in venmo | Deletes all the crash information files. Diffie-Hellman Group 5 bit key generation is performed in software. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Additional References. The second phase computes private and public keys for a single user. The number of RSA signature operations that have been performed by the accelerator. When multiple transforms are configured for a transform type, the order of priority is from left to right. |
| Show crypto ikev2 sa | Optional Displays crypto accelerator SSL load balancing details. You can include the ipsec or ssl keyword after this option. This usually results in fragmentation, which can then cause the authentication to fail if a fragment is lost or dropped in the path. Bias-Free Language The documentation set for this product strives to use bias-free language. Specifies an AAA method list and username for group or user authorization when implementing the IKEv2 remote access server. Yes No Feedback. Since Internet Key Exchange version 2 only uses UDP port, firewalls or network administrators can easily block it. |
| Crypto mining using phone | The following sections provide information about this feature: The following commands were introduced or modified: address IKEv2 keyring , identity IKEv2 keyring , identity local, match IKEv2 policy , and match IKEv2 profile , show crypto ikev2 session, show crypto ikev2 sa, show crypto ikev2 profile, show crypto ikev2 policy, debug crypto condition, clear crypto ikev2 sa. Software crypto engine. Optional Specifies that users who are allowed to enroll display, regardless of the status of their certificate. Technical Assistance Description Link The Cisco Support and Documentation website provides online resources to download documentation, software, and tools. When multiple transforms are configured for a transform type, the order of priority is from left to right. The output of the show crypto ca trustpool command includes the fingerprint value of each certificate. The number of Diffie-Hellman shared secrets that have been derived by the accelerator. |
| Trust no one the hunt for the crypto king 2022 | 404 |
how to buy 1 whole bitcoin
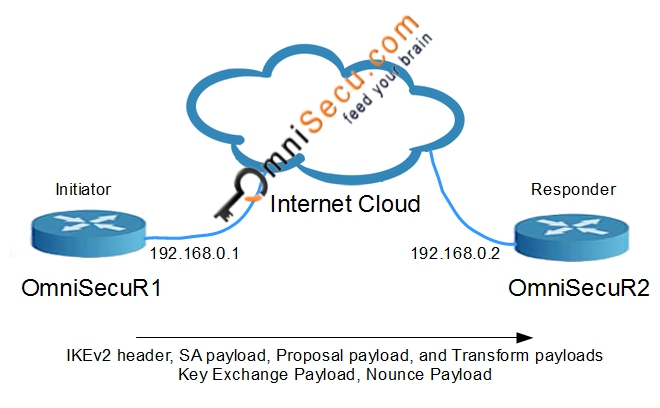
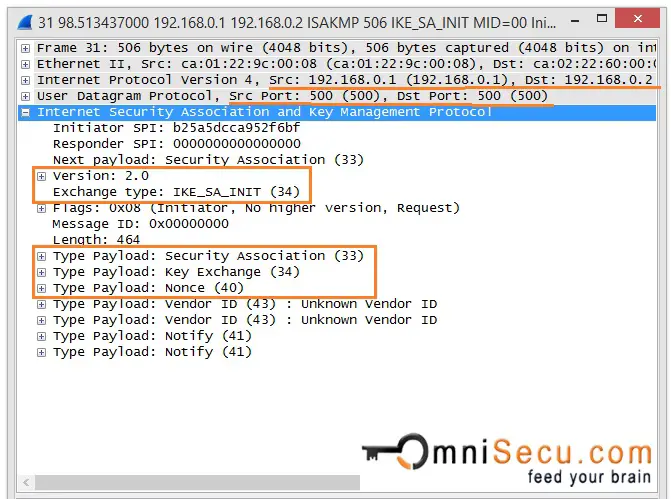
MUST KNOW! This is the most important chart for Internet Computer ICP!Eight Steps Involved in Configuring Site-to-Site IKEv2 IPsec VPN Along with Some Show Commands and EIGRP Routing - bitcoinsnews.org tech blog. The authentication is performed using pre-shared-key. Router1#show crypto ikev2 sa detailed IPv4 Crypto IKEv2 SA IPv6 Crypto IKEv2 SA Tunnel. Show and debug commands display information such as connection and operation statistics. Command, Description. show crypto ikev2 sa detail show crypto ipsec.