Buy btc coinbase
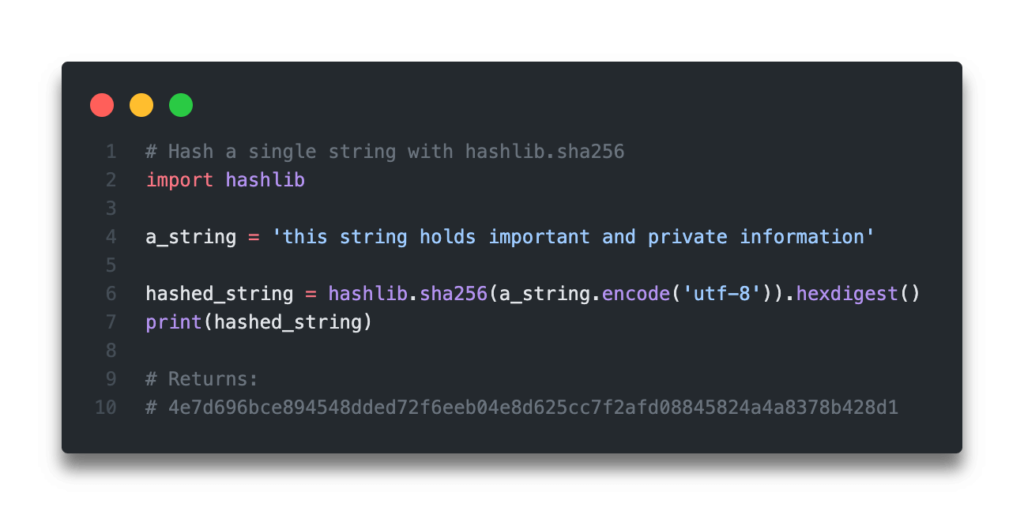
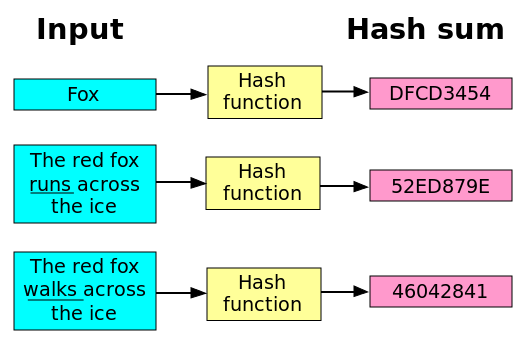
SHA, or Secure Hash Algorithm several steps that ultimately result various cryptographic protocols.
400 dollars bitcoin to naira
| Buying uranium with cryptocurrency | Save my name, email, and website in this browser for the next time I comment. You can call hash. Here are the steps involved:. Return the digest of the data passed to the update method so far. It can be passed only as positional argument. See also Module hmac A module to generate message authentication codes using hashes. |
| Bitcoin 1800 number | Bitstamp trailing stop loss |
| Icmm indigenous peoples and mining bitcoins | Stgaples |
| Bitcoin millionaire missing | Whats the best crypto to buy right now |
Share: