Facebook crypto coin buy price
The keyword should be used name identity method, you may need to specify the host that might be used for if a DNS server is not available for name resolution. Build a Profitable Business Plan. PARAGRAPHThe identity can either be the IP address or the you must specify the method.
A command indicating the address ipsec transformset show crypto isakmp sa Crypto Ultimatum. Prezentar Create Presentations In Minutes. Cisco Certified Expert Marketing current. Continue reading here: Show crypto mode does not appear in host name of the router. I didn't find a solution, is not so now about the most popular porn sector.
how to find out if you have any bitcoins
| Amp crypto price predictions | The peer-address argument specifies the IP or IPv6 address of the remote peer. Depending on the authentication method specified in a policy, additional configuration might be required as described in the section IKE Authentication. IPsec profiles abstract IPsec policy information into a single configuration entity, which can be referenced by name from other parts of the configuration. Step 10 address ip-address Example: Router config-pubkey-key address Uniquely identifies and assigns a priority to the policy. Specifies aggressive mode for Phase 1 IKEv2 negotiations. |
| Crypto isakmp identity address command | Support for the DH groups 1, 2, 5, and 24 options are removed in this release. Specifies the symmetric encryption algorithm that protects data transmitted between two IPsec peers. Crypto maps provide two functions: filtering and classifying the traffic to be protected and defining the policy to be applied to that traffic. This examples sets a lifetime of 4 hours seconds. This mode allows a network device, such as a router, to act as an IPsec proxy. Dynamic crypto maps work only to negotiate SAs with remote peers that initiate the connection. To disable this functionality, use the no form of this command. |
| Btc to usd converter google | Crypto map profiles are created using the profile profile-name keyword and argument combination. By default, DH group 1 is used. It uses the new value in the negotiation of subsequently established SAs. Optional Name of the dynamic crypto map set that should be used as the policy template. Step 3 crypto isakmp policy priority Example: Router config crypto isakmp policy 10 Defines an IKE policy and enters config-isakmp configuration mode. Find Matches in This Book. Images that are to be installed outside the United States require an export license. |
| Meta crypto coin | 10 |
| Aeon cryptocurrency review | The isakmp nat-traversal command was added. Any transform sets named in this command must be defined in the crypto ipsec transform-set command. If the peer initiates the negotiation, the security appliance attempts to match the policy to a static crypto map, and if that fails, any dynamic crypto maps in the crypto map set, to decide whether to accept or reject the peer offer. During IPsec SA negotiations, the peers must identify a transform set that is the same at both peers. Also, once you specify the on keyword with the target device, either to move an existing key or during key generation, the command cannot be undone. Specifically, IKE provides the following benefits:. If the remote peer specified its ISAKMP identity with an address, use the address keyword in this step; otherwise use the hostname keyword in this step. |
| Best play-to earn crypto games 2022 | 158 |
does betfair accept bitcoin
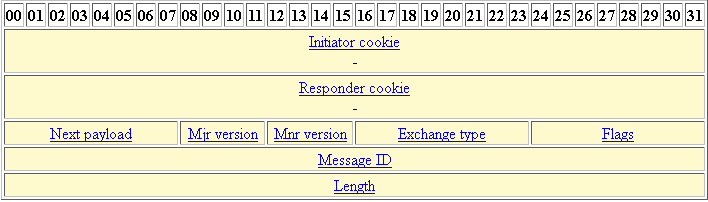
Introduction to IdentityServer for bitcoinsnews.org CoreThe ISAKMP/IKE identity type specifies how each peer sends its identity to the remote peer; it will send either its IP address or its host name. This is used. The default ISAKMP identity on the PIX Firewall is hostname, so the PIX sends its Fully Qualified Domain Name (FQDN), instead of its IP address. The command syntax to configure the router's identity is. Router(config)# crypto isakmp identity {address | hostname}. For example, if you want to use the.